Boost Your Risk Management: Streamline Security with Integrated Cybersecurity Tools
In today’s fast-paced digital world, businesses are constantly facing new and evolving cyber threats. As technology advances, so do the tactics used by cybercriminals. This makes having a solid risk management strategy more important than ever. But what does it mean to integrate cybersecurity tools into this strategy?
In this blog, we will explore how integrating these tools can help create a unified risk management strategy that not only protects your organization but also enhances its overall efficiency.
Understanding Integrated Risk Management iRM
Integrated Risk Management iRM is a comprehensive approach that allows organizations to identify, assess, and manage risks across various domains, including cybersecurity.
Unlike traditional risk management methods that often operate in silos, iRM promotes a holistic view of risk. This means that instead of addressing risks individually, organizations can see the bigger picture and understand how different risks interact with one another.
Why is iRM Important in Cybersecurity?
As cyber threats become more sophisticated, organizations need to adopt strategies that enable them to respond effectively. iRM helps businesses align their cybersecurity efforts with broader organizational goals. It fosters collaboration between different departments, such as IT and operations, ensuring everyone is on the same page when it comes to risk.
For example, by integrating cybersecurity into the overall risk management framework, organizations can make informed decisions that protect critical assets while ensuring compliance with regulations. This approach not only enhances security but also improves operational efficiency.
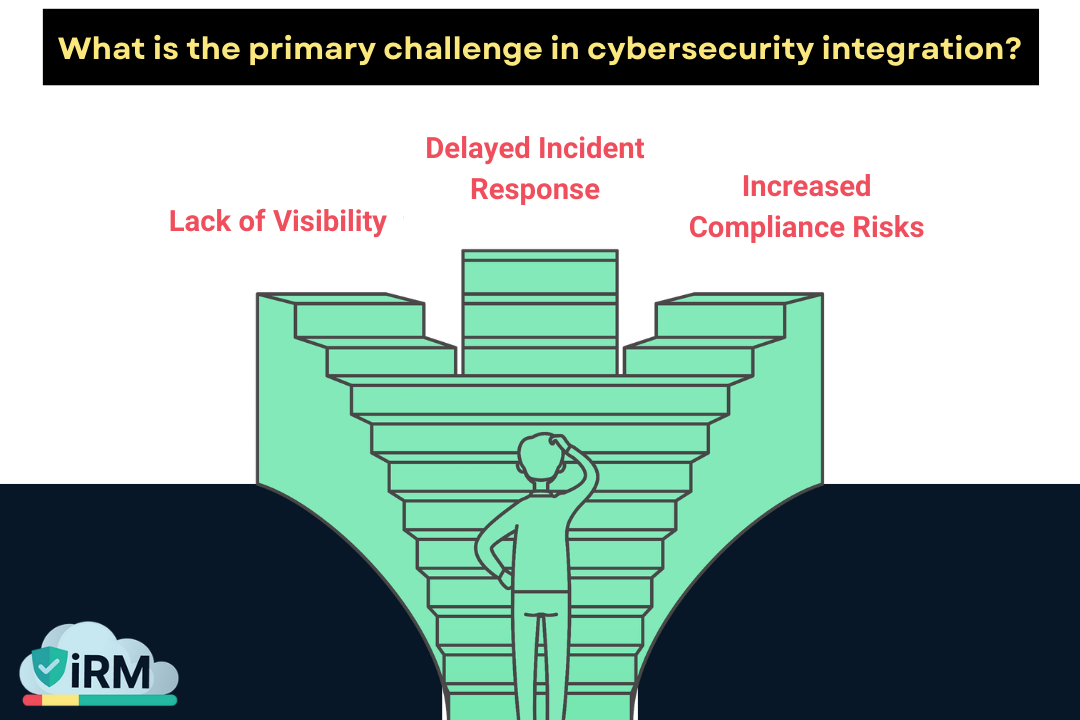
The Need for Integration of Cybersecurity Tools
Many organizations use various cybersecurity tools to protect their assets. However, when these tools operate independently, it can lead to gaps in security and inefficiencies in response times. Here are some challenges associated with siloed approaches:
- Lack of Visibility: When tools don’t communicate with each other, it’s hard to get a clear picture of the organization’s security posture.
- Delayed Incident Response: If different teams are using different tools, it can slow down the response time when a threat is detected.
- Increased Compliance Risks: Managing compliance becomes more complicated when tools are not integrated.
Benefits of Integration
Integrating cybersecurity tools into a unified risk management strategy offers several benefits:
- Enhanced Visibility: A unified approach provides better visibility into potential threats across the organization.
- Improved Incident Response: With all tools working together, organizations can respond to incidents more quickly and effectively.
- Streamlined Compliance Management: Integrated systems simplify compliance efforts by ensuring that all tools adhere to regulatory requirements.
Key Cybersecurity Tools for Unified Risk Management
To create an effective unified risk management strategy, organizations should consider several key cybersecurity tools:
- Security Information and Event Management (SIEM) - SIEM systems collect and analyse security data from across the organization in real-time. They provide insights into potential threats and help security teams respond promptly.
- Threat Intelligence Platforms - These platforms aggregate data from various sources to provide context about potential threats. By understanding the threat landscape, organizations can better prepare for attacks.
- Automated Risk Assessment Tools - Automated tools streamline the process of identifying and assessing risks. They help organizations stay ahead of potential issues by providing regular updates on their security posture.
- Incident Response Management Systems - These systems help organizations manage security incidents from detection through resolution. They ensure that teams can collaborate effectively during an incident. By integrating these tools with existing systems like Oracle Fusion and SAP, organizations can create a seamless flow of information that enhances their overall security posture.
Steps to Create a Unified Risk Management Strategy
Creating a unified risk management strategy involves several key steps:
Step 1: Assess Current Cybersecurity Landscape
Start by conducting a comprehensive risk assessment to understand your organization’s current security posture. Identify vulnerabilities and areas for improvement.
Step 2: Identify Integration Opportunities
Evaluate existing cybersecurity tools and look for gaps in integration. Determine which tools can be connected to enhance visibility and response times.
Step 3: Develop a Strategic Plan
Outline a roadmap for integrating these tools into a cohesive strategy. Consider best practices from industry leaders and tailor your approach to fit your organization’s needs.
Step 4: Implement and Monitor
Once your plan is in place, begin implementing the integration of your cybersecurity tools. Continuously monitor their effectiveness and make adjustments as needed.
Overcoming Common Challenges in Integration
Integrating cybersecurity tools can come with its own set of challenges:
- Resistance to Change: Employees may be hesitant to adopt new systems or processes.
- Resource Constraints: Limited budgets can make it difficult to invest in new technologies.
- Maintaining Compliance: Ensuring compliance while integrating new tools can be complex.
To overcome these challenges, it’s essential to communicate the benefits of integration clearly and provide adequate training for staff members.
Measuring Success in Integrated Risk Management
Once you have implemented your unified risk management strategy, it’s important to measure its success. Here are some key performance indicators (KPIs) to consider:
- Reduction in Incident Response Times: Track how quickly your team responds to incidents before and after integration.
- Improved Compliance Scores: Monitor compliance metrics to ensure that your organization meets regulatory requirements.
- Enhanced Employee Awareness: Evaluate training programs to see if employees are more aware of cybersecurity practices.
Integrating cybersecurity tools into a unified risk management strategy is not just beneficial; it’s essential in today’s digital landscape. By taking a holistic approach to risk management, organizations can enhance their security posture while improving operational efficiency. If you’re ready to take the next step toward creating a unified risk management strategy for your organization, we at iRM are here to help! Our team specializes in providing integrated solutions tailored to meet your unique needs.
Don’t wait until it’s too late! Reach out today through our Contact Us page and let us help you safeguard your organization against cyber threats while streamlining your risk management efforts!
.png)
