Lock Down Your Response: Proven Steps To Prevent Change Healthcare-Style Breaches
Every organization handling sensitive data knows that a single cyber incident can cascade into massive financial losses, damaged reputations, and disrupted operations. Change Healthcare’s February 2024 ransomware attack—which cost an average of $353,000 per incident in downtime, fines, and recovery—highlights how gaps in incident management can multiply the harm a breach inflicts .
As ransomware gangs adopt double-extortion tactics and regulators demand faster breach disclosures, companies must overhaul their response playbooks. Let’s break down what went wrong, what’s changing in 2025, and how you can build an incident management strategy that stops ransomware in its tracks—culminating in a simple call to action: reach out to iRM for tailored guidance.
The True Cost of Reactive Response
In early 2024, Change Healthcare—a key processor of medical claims—fell victim to the ALPHV/BlackCat ransomware gang. The attackers encrypted critical systems and exfiltrated patient data, grinding claims processing to a halt for weeks. Each day of downtime, combined with regulatory fines and forensic costs, added up to roughly $353,000 per incident .
This wasn’t a one-off statistic. The FBI’s 2025 ransomware report shows average ransom demands rising above $500,000, with total recovery costs often exceeding $1 million per event . Against that backdrop, the question isn’t if you’ll face ransomware—it’s when. And if your incident management plan isn’t battle-tested, that “when” could be a financial and reputational disaster.
Breach Timeline: From Initial Compromise to Aftermath
- February 21, 2024: A targeted spear-phishing email delivers the initial foothold, slipping past legacy email filters.
- Late February – Early March: Attackers move laterally, harvest credentials, and probe backup systems without raising alarms.
- March 10: Ransomware is deployed, encrypting billing, claims, and patient-eligibility servers.
- March 12–20: IT teams scramble to isolate infected networks, relying on manual containment steps that prolong outage.
- March 21: Public breach notification is issued, triggering regulatory deadlines and customer outreach efforts.
Each passing day of unplanned downtime cost Change Healthcare millions—and eroded trust among its 131 million affected patients and 67,000 partner pharmacies .
Where Traditional Frameworks Fell Short
Most organizations lean on standards like NIST SP 800-61 for incident management guidance. Yet Change Healthcare’s response exposed key gaps:
- Delayed Detection: Manual log reviews meant early warning signs went unnoticed for weeks.
- Siloed Communication: Legal, IT, and executive teams exchanged updates in slow, sequential channels—delaying critical decisions.
- Lack of Automation: Without AI-driven threat hunting or orchestration, teams were stuck in reactive mode.
- Unprepared Negotiation: Absence of pre-approved negotiation protocols led to a reported $22 million ransom payment—far above industry averages .
These missteps turned a manageable breach into a months-long crisis. The remedy? Integrate real-time detection, cross-functional drills, and automated playbooks to shrink your “blast radius” when attackers strike.
Ransomware’s New Reality: 2025 Trends to Watch
Ransomware gangs are evolving fast. In 2025, expect:
- Double-Extortion Tactics: Attackers encrypt data and threaten to make it public unless paid.
- AI-Enhanced Phishing: Machine learning crafts ultra-targeted lures that bypass basic filters.
- Supply-Chain Strikes: Hitting smaller vendors to breach large enterprises—just as BlackCat did at Change Healthcare.
- Regulatory Crackdown: The SEC now demands breach disclosures within 72 hours or faces multi-million-dollar fines .
To keep pace, incident plans must evolve from static checklists into live, high-pressure simulations—testing data-leak safeguards and rapid public-notification workflows.
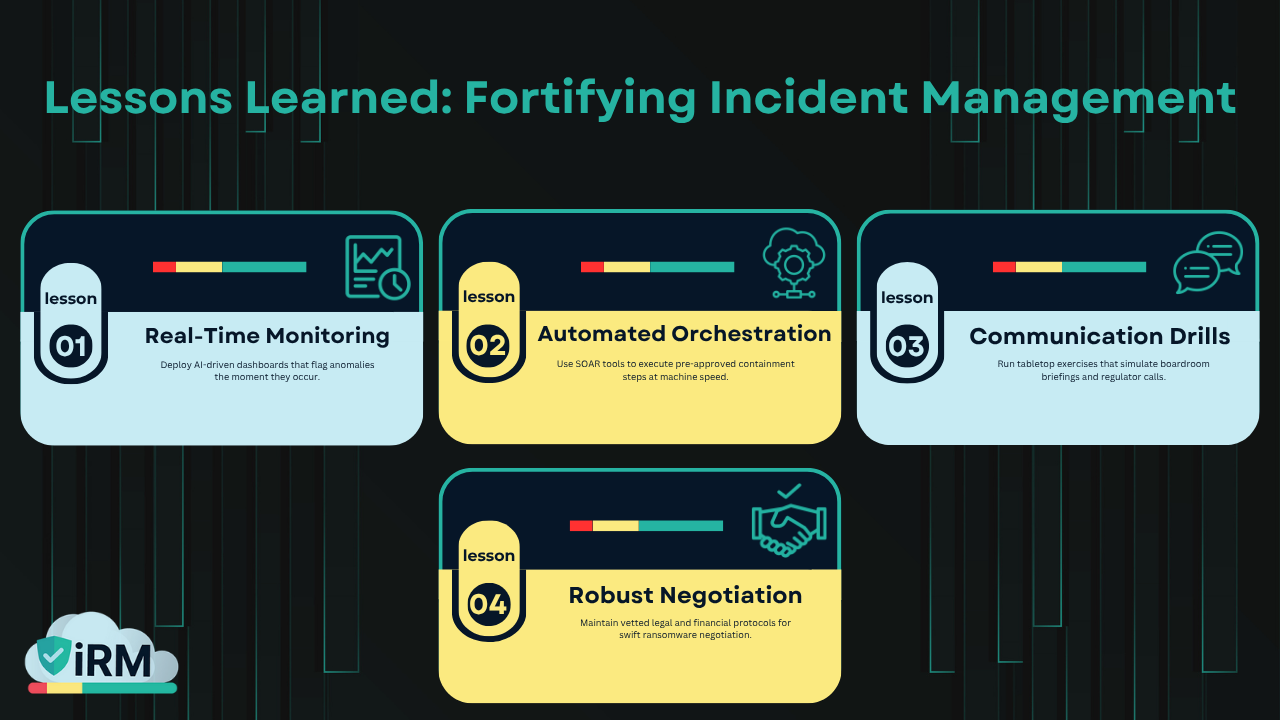
Lessons Learned: Fortifying Incident Management
From Change Healthcare’s ordeal, four clear lessons emerge:
- Real-Time Monitoring: Deploy AI-driven dashboards that flag anomalies the moment they occur.
- Automated Orchestration: Use SOAR tools to execute pre-approved containment steps at machine speed.
- Communication Drills: Run tabletop exercises that simulate boardroom briefings and regulator calls.
- Robust Negotiation Plans: Maintain vetted legal and financial protocols for swift ransomware negotiation.
Embedding these measures shifts your stance from firefighting to fire-prevention, cutting incident damage by up to 80% .
Proactive Tools: Sentinel, GenAI, and Beyond
Leading organizations layer next-gen tools onto their incident response:
- Microsoft Sentinel: Automates detection across cloud and on-premises and triggers containment workflows in minutes .
- GenAI Playbooks: Large-language models draft incident summaries, customer notifications, and regulator filings in hours instead of days.
- Threat Intelligence Feeds: Combine open-source and commercial feeds for 360° visibility into emerging BlackCat tactics.
Pilot these in a safe test environment to measure time savings and refine handoffs between humans and machines.
Navigating Regulatory Demands
In today’s landscape, incident management and compliance converge. Public companies face the SEC’s cybersecurity rules, which require timely and accurate disclosures of material cyber incidents to protect investors. Healthcare organizations under HIPAA must notify affected individuals and the Department of Health and Human Services within tight deadlines when patient data is involved. And any breach affecting EU citizens triggers GDPR’s strict 72-hour notification window, with potential fines up to 4% of global turnover for late or inadequate reporting. Balancing these overlapping requirements under pressure demands pre-approved notification templates, clear approval chains, and a single source of truth for breach details—so when regulators or customers ask questions, you respond with confidence and speed, rather than scrambling for information.
Building an Unbreakable IR Program
Your final blueprint should include:
- Governance & Roles: Define clear incident leadership—C-Suite sponsors, IR leads, and communication owners.
- Regular Drills: Hold quarterly live and tabletop exercises covering encryption, data-leak, and supply-chain scenarios.
- Continuous Improvement: Post-mortem reviews feed insights back into detection rules and playbooks.
- Vendor Assurance: Require key third parties to maintain their own incident plans and share drill outcomes.
This cycle of preparation, response, and learning turns a static IR plan into a living, adaptive defense.
Ransomware is not a question of if, but when. When the next BlackCat or LockBit hits your network, a battle-ready incident management plan can mean the difference between a brief hiccup and a headline-making catastrophe.
Don’t let another breach drain your resources and reputation. Connect with iRM to build a custom incident response platform—complete with AI-powered dashboards, GenAI-driven playbooks, and boardroom governance—so you stop ransomware before it stops you.
👉 Reach out to us for expert incident management consulting
.png)
