The Cyber Threats You Don’t See Coming: 5 Must-Know Cyber Risk Trends
Hey there! As we step into February 2025, it’s the perfect time to spotlight something that never goes out of season—cybersecurity.
Forget ghosts and goblins; we’re talking cyber threats that creep up like shadows in the dark. This year, we’re excited to chat about five big cybersecurity trends you need to know about. Whether you’re running a business, surfing the web, or just curious, these trends might hit close to home. So, grab a coffee, kick back, and let’s dive into this together—it’ll be fun, easy to follow, and packed with stuff worth knowing!
Trend 1: AI-Driven Cyber Threats
Let’s start with AI-driven cyber threats. You know artificial intelligence—AI—the tech that suggests your next binge-watch or predicts your texts. Pretty slick, right? But here’s the kicker: cybercriminals are jumping on the AI bandwagon, and not in a good way.
Imagine hackers using AI to craft phishing emails so convincing they could fool your grandma—or even you! These messages might trick you into clicking a shady link or handing over sensitive info. Then there’s deepfakes—AI-made fake videos or audio. Picture a video of your CEO asking for urgent funds, but it’s all a sham. Creepy stuff!
We’ve seen reports from 2023 showing a 30% spike in phishing attempts, all thanks to AI tools making attacks smarter. But don’t worry—the good guys are fighting back with AI too, spotting weird data patterns and yelling “intruder!” before things get messy. It’s like a superhero showdown: AI’s got power, but it’s all about who wields it best. Stay sharp, and maybe grab some AI-powered defenses to keep the bad guys out.
Trend 2: Ransomware Evolution
Next, let’s talk about ransomware evolution. If you’re new to the term, ransomware is like a digital kidnapper—it locks your files and demands a ransom to unlock them. It’s been around a while, but lately, it’s leveled up in a nasty way.
Now, hackers don’t just lock your data—they steal it too. It’s called double extortion: “Pay us, or we’ll spill your secrets online.” Ouch! We came across a jaw-dropping stat: in 2022, ransomware cost businesses over $20 billion, with average payouts of around $150,000—not counting the cleanup chaos.
Remember the Colonial Pipeline attack in 2021? Hackers shut down a huge fuel line for a big payday, causing panic at the pumps. It’s not just giants getting hit—small businesses and everyday folks are targets too. Our advice? Keep software updated, back up your files somewhere safe, and don’t touch suspicious emails. It’s like locking your car and keeping a spare tire handy—basic moves that save the day.
Trend 3: IoT Vulnerabilities
Time to tackle IoT vulnerabilities. IoT—Internet of Things—is the fancy label for connected gadgets like smart thermostats, security cams, or that fridge that nags you about milk. Awesome, right? But here’s the downside: these toys can be a hacker’s jackpot.
Lots of IoT devices ship with flimsy security—think passwords like “password123” or no updates to patch holes. Hackers love that. Ever hear of the Mirai botnet? In 2016, it turned thousands of IoT gadgets—like routers and cameras—into a zombie army that knocked big websites offline. Wild!
We read that by 2025, there could be 75 billion connected devices out there. That’s a ton of weak spots! To lock it down, swap those default passwords ASAP, keep devices updated, and maybe put them on a separate Wi-Fi network. It’s like keeping your snacks in a safe—keeps the sneaky hands away.
Trend 4: Supply Chain Attacks
Now, onto supply chain attacks. These are clever—hackers don’t target you directly; they hit your suppliers first. It’s like sneaking into your office through the delivery guy’s truck. Once they’re in, they can waltz into your systems too.
Take the SolarWinds attack in 2020—hackers tampered with a software update, putting thousands of companies and government offices at risk. Or the Kaseya attack in 2021, which spread from a tech provider to hundreds of businesses. These hits are sneaky because they come through trusted channels.
Our take? Quiz your vendors on their security game and keep an eye on your own network for funky stuff. It’s like checking your mail for tampered packages—stay curious and cautious.
Trend 5: Zero-Trust Architecture
Finally, let’s explore zero-trust architecture. Sounds hardcore, huh? It’s a simple idea: trust no one. Even if someone’s inside your network—like a coworker or a device—we keep verifying them. No VIP passes here!
Old security was like a fortress—get past the wall, and you’re golden. Zero-trust says, “Prove it, every step.” It’s brilliant for stopping insider threats or hackers who sneak in. Studies show zero-trust cuts breaches by up to 50%. Not bad!
Start easy: add multi-factor authentication (like a code to your phone) and limit access to just what’s needed. It’s like handing out specific keys, not the master set. With threats getting craftier, zero-trust is our kind of smart.
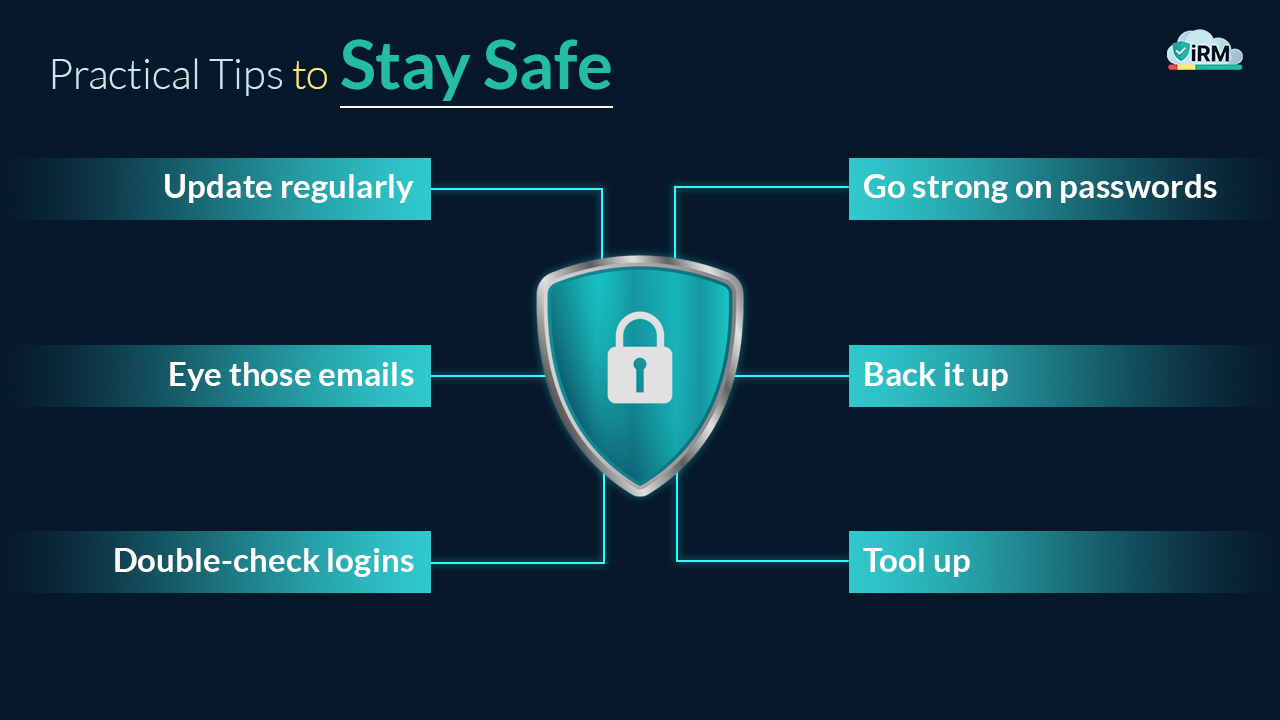
Practical Tips to Stay Safe
Okay, we’ve hit the big five—now what? Here are some quick tips to armor up against these cyber risks:
- Update regularly. Fresh software plugs holes hackers exploit.
- Go strong on passwords. Mix letters, numbers, and symbols—make it tough!
- Eye those emails. If it’s off, trash it—no clicks.
- Back it up. Save files so ransomware’s just an annoyance.
- Double-check logins. Multi-factor authentication is your buddy.
- Share the love. Teach your crew these tricks—teamwork wins.
- Tool up. Antivirus and firewalls are your digital bouncers.
It’s like keeping your house tidy—small habits, big protection.
There you go—Cybersecurity Month gives us a peek at the wild cyber landscape. We’ve covered AI-driven threats, ransomware’s new tricks, IoT weak spots, supply chain sneakiness, and zero-trust smarts. Each one’s a different beast, but they all say the same thing: stay alert.
The upside? You’re not alone in this. With some know-how and easy steps, we can keep you—and your business—safe. It’s about being proactive, not paranoid. And if it feels like a lot, that’s why we’re here at iRM—to swoop in and help.
Why wait for the cyber creeps to strike? Take control now! Whether it’s outsmarting AI scams or securing your smart gadgets, we’ve got your back at iRM with killer solutions. Swing by our Contact Us page today—let’s team up to make your digital life a hacker-proof fortress. Your calm, cool, and collected future is one click away!
.png)
